In part one of this series, I discussed and walked through setting up an AWS instance to crack captured password hashes. In this installment, I’ll discuss two popular applications that can be used for cracking and walk through installing them on Ubuntu.
Hashcat is widely known for its speed and flexibility. It supports a range of hash types and takes full advantage of GPU acceleration, making it ideal for cracking large hash dumps. With support for rule-based, dictionary, brute-force, and hybrid attacks, Hashcat is favored by professionals who need efficiency and scalability. However, it’s hardware-intensive and can be intimidating for beginners due to its complex syntax and command-line interface.
John the Ripper (JtR), on the other hand, is more versatile in terms of file formats and system compatibility. It handles not only hashes but also password-protected files and full disk images. Its "Jumbo" version offers extended functionality with support for hundreds of formats. JtR is especially useful in forensic or offline cracking contexts. While it doesn’t match Hashcat’s GPU-driven speed, it offers deep customization and robust rule-based attacks.
For our purposes, we will be using Hashcat in order to take advantage of the GPU processing provided by our AWS instance. While a version of Hashcat is present in the Ubuntu repository, I recommend compiling it from source to ensure that you have the latest version. To install run the following commands:
• Update the Ubuntu repositories:
o sudo apt update
• Install the git utilities:
o sudo apt install -y build-essential git
• Clone the Hashcat application:
o git clone https://github.com/hashcat/hashcat.git
• Switch to the Hashcat directory
o cd hashcat
• Compile and install:
o make
o sudo make install
Now that Hashcat is installed, it’s necessary to install the GPU drivers and the CUDA toolkit to take advantage of the GPU processing power in the instance.
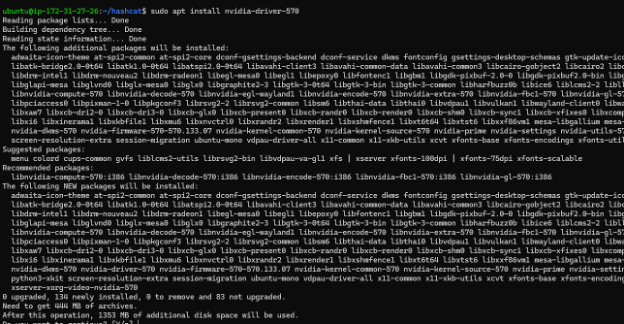
• Install Nvidia Drivers:
o Sudo apt install nvidia-driver-<current driver version>:
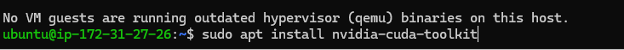
• Install the CUDA toolkit:
o sudo apt install nvidia-cuda-toolkit
Now your instance is setup to begin using Hashcat to crack passwords. In the next installment, I will demonstrate finding wordlists and rules for dictionary attacks.




















