Utilities Sector
Services and solutions uniquely crafted to meet the high availability and safety standards of the Utility Sector.


Critical Infrastructure Utilities
We partner with electric distribution cooperatives, generation and transmission providers, and water utilities to strengthen their cybersecurity posture and manage operational risk in an increasingly complex threat environment. Through comprehensive security testing engagements, in-depth risk assessments, and tailored annual programs designed specifically for the utility sector, we help our clients identify and prioritize vulnerabilities that could jeopardize their operations, compromise customer data, or disrupt the essential services their communities depend on.
Our team brings over 20 years of specialized experience within the utility landscape, combining deep knowledge of operational technology environments, regulatory frameworks like NERC CIP and AWWA standards, and emerging cyber threats targeting critical infrastructure. We don't just identify risks—we transform visibility into actionable strategy, providing clear remediation roadmaps and ongoing support that enable utilities to protect their systems, satisfy compliance requirements, and build resilience against both current and evolving threats.
Whether you're managing substations and SCADA networks, smart grid deployments, or water treatment facilities, we're committed to helping you secure the infrastructure that powers and sustains daily life.
Services and Solutions Specific to Your Industry
Utilities Sector Security Assessment

The Foundation of Effective Security Programs
Every robust security program should be built on two fundamental activities performed at least annually: a comprehensive Risk Assessment and a thorough Penetration Test. Together, these complementary exercises form the cornerstone of organizational cybersecurity.
A Risk Assessment documents your security controls, policies, and intended operational safeguards—essentially mapping what should protect your environment. The Penetration Test validates whether those controls actually work as intended in real-world scenarios. One identifies and documents your defenses; the other proves their effectiveness. Without both, organizations operate with an incomplete picture of their security posture.
Utilities Sector Assessment Overview
Our Utilities Sector Assessment is a specialized adaptation of our flagship Penetration Testing service, developed in alignment with the Open-Source Security Testing Methodology (OSSTM) and the Penetration Testing Execution Standard (PTES). Beyond the core penetration testing components, this assessment incorporates three critical utilities-specific activities: Segmentation Testing, Substation Auditing, and Ransomware Readiness Review. As with all our enterprise solutions, the engagement concludes with a formal presentation and executive briefing to organizational stakeholders.
Actionable Results and Prioritization
The penetration test deliverables include a detailed remediation plan with both short-term and long-term activities, enabling organizations to effectively prioritize key areas of concern when resources are limited. For core security issues identified, we provide both OPex and CAPex context to support informed budgeting and resource allocation decisions.
Regulatory and Insurance Considerations
These annual assessments are often mandated by regulatory frameworks like NERC CIP and are increasingly required by cyber insurance carriers. Failure to perform them can result in fines, coverage denials, and claim rejections.
Utilities Sector Critical Controls Risk Assessment

Strategic Visibility
As utilities face sophisticated cyber threats and evolving regulations, understanding your security posture is critical. Our assessment gives leadership strategic visibility to make informed decisions about risk management and resource allocation.
Why Annual Assessments Matter
Utilities operate in dynamic environments where threats evolve, infrastructure expands, and regulations shift. Annual assessments ensure you maintain current visibility as new assets come online, vulnerabilities emerge, staff transitions occur, and threat actors develop new techniques.
Key Benefits
- Meaningful Visibility: Translate technical risks into business impact so executives understand your security posture and critical priorities
- Environmental Understanding: Map your OT and IT environments, including assets, data flows, and operational interdependencies
- Gap Identification: Uncover control deficiencies before exploitation, with a roadmap for targeted remediation
Complementary Penetration Testing
Assessments evaluate control design and implementation; penetration testing validates effectiveness. Together, they provide strategic insight and tactical validation—showing where controls should exist and whether they actually work against real attacks.
Flexible Framework Approach
We understand that different utilities operate under various complianceregimes and organizational structures. Our assessment methodology is framework-agnostic and can be tailored to align with your existing governance approach, including:
- NIST Cybersecurity Framework
- CIS Critical Security Controls
- ISO/IEC 27001
- Custom operational frameworks
This flexibility ensures the assessment integrates seamlessly with your existing compliance efforts and speaks the language your organization already uses for risk management.
Deliverables
Receive comprehensive reporting with risk ratings, control maturity assessments, prioritized recommendations, and executive summaries—a strategic roadmap aligned with business objectives.
Ready to gain visibility into your critical controls? Contact us to discuss tailoring our assessment to your utility's operational environment.
Utilities Sector Incident Response Impact Simulation

Prepare for incidents before they happen—test your response and quantify your risk.
Contextual Security Solutions's Incident Response Impact Simulation (IRIS) is a comprehensive incident response analysis engagement that combines a tabletop exercise with an in-depth review of your utility's incident response plan.
Regular testing of incident response procedures is critical to operational resilience in the critical infrastructure sector. Utilities that routinely conduct tabletop exercises are better prepared to respond effectively during actual incidents—whether cyber-attacks, physical security breaches, or cascading system failures—reducing both response time and overall impact to essential services. Beyond operational readiness, these exercises demonstrate due diligence to regulators and can positively influence cyber insurance premiums and coverage terms. Many compliance frameworks—including NERC CIP, NIST Cybersecurity Framework, and sector-specific regulations—require or strongly recommend regular incident response testing.
IRIS goes beyond traditional tabletop exercises by providing a detailed analysis of potential financial and operational impacts identified during the simulation. This includes quantifying costs associated with:
- Critical system downtime and service interruption to customers
- Loss of operational capacity and employee productivity
- Equipment damage, replacement, and expedited procurement expenses
- Regulatory fines, penalties, and mandatory reporting costs
- Recovery and remediation expenses
- Additional costs specific to utility operations and your scenarios
We also provide contextualized analysis of the financial, reputational, and public safety costs associated with sensitive data disclosure, including customer information, operational technology data, and critical infrastructure details. This helps leadership understand the full scope of risk exposure unique to utility operations, including impacts on public trust, regulatory standing, and community safety.
All findings are documented in a formal report that includes actionable recommendations for strengthening your incident response capabilities within the context of 24/7 operations, SCADA/ICS environments, and coordination with emergency management agencies. The engagement concludes with an executive briefing designed to communicate key insights and strategic priorities to senior leadership, board members, and relevant regulatory stakeholders.
Utilities Sector B.A.S.E. Annual Program

The Base Assessment of Security Elements (BASE) X program is a security as a service offering (billed monthly) curated by Contextual Security Solutions. The primary goal is to create a foundation within your utility organization's information security program that allows it to effectively maintain visibility into operational technology (OT) and information technology (IT) risks and exposures, while also improving cybersecurity and compliance postures.
The BASE X program is composed of three (3) key components: Core Services, Targeted Assessments and Executive Briefings. Core Services are those broad foundational security tasks that every utility organization should be performing regardless of size or service territory, on an annual basis. This primarily includes Critical Control Risk Assessments with a focus on grid reliability and operational continuity, and Red Team Exercises that simulate attacks against both IT and OT environments including SCADA systems, substations, and control centers.
Targeted Assessments are precision-focused engagements that center on specific security domains critical to utilities operations (e.g., Incident Response for cyber-incidents, Attack Visibility across IT/OT environments) and are geared toward responding to emerging threats targeting critical infrastructure, addressing specific NERC CIP or other regulatory compliance requirements, or strengthening particular aspects of your utility security program.
Executive Briefings are strategic sessions for discussing the results from the Core Services and Targeted Assessments and providing actionable insights tailored specifically to your utility's operational environment, risk tolerance, and regulatory obligations.
A key feature of the BASE X program is its flexibility. What your utility organization chooses within these engagement groups is completely dependent on your specific needs, whether you operate generation, transmission, distribution, or a combination thereof. In addition, these components can be changed at any time as your utility operations and the unique threat landscape facing critical energy infrastructure shifts. However, one facet that will remain unchanged throughout the life of the BASE X program will be Contextual Security Solutions' team of Security & Compliance consultants—with deep expertise in utilities sector cybersecurity and OT security—providing premium, subject matter expertise for your organization during our Executive Briefings.
At Contextual Security Solutions, we want to be more than a vendor, we want to be your SecurityXtension—your trusted partner in protecting critical energy infrastructure and ensuring grid resilience.
Utilities Sector Community Involvement
Contextual Security Solutions actively engages with our customer community by providing education and empowering them with the resources and tools needed for proactive change. Our commitment to partnership through education extends to utility and critical infrastructure providers at the local, state, and national levels.
We have been privileged to serve as featured speakers at some of the utility sector's largest national events, including NRECA Tech Advantage and NRECA Co-op CyberTech. We have also presented at state and regional conferences such as the Alabama Rural Electric Association of Cooperatives (AREA) Annual Meeting, Georgia EMC, Kansas Electric Cooperatives, Texas Electric Cooperatives, and the Cooperative Technologies Conference & Expo (CTCE) in the Carolinas. Additionally, we are regular contributors to education conferences such as CyberCon and have led workshops at EnergySec's Security Education Week.

Here are some of our recent presentations:
- A.I. Isn’t as Smart as You Want it To Be
- Common Security Findings in Industrial Control Systems (ICS)
- Zone 3 Expo “Parsing Data from Common Security Tools"
- The Blue Team Never Sleeps
- Emerging Utility Threat landscape
- From Password123 to Secure Fortress
- Email Security Best Practices
- CbryeScretuiy | Nkwo Hte Ismsoin" (Cybersecurity-Know the Mission)
- Security Metrics and Budget Implications
- Common Assessment Tools for IT and OT Testing
Substation Audits
How Vulnerable Are Your Substations?
Physical attacks on the U.S. Power grid have increased significantly over the past decade. Cyber events, sabotage, physical attacks, vandalism, and other human related disturbances have all contributed to the uptick. Just five years ago, the total number of all human related disturbances reported to DOE (via form OE-417) was just under sixty (60). In 2023, that number was close to 200, with several targeting substations. How vulnerable are your substations? What kind of visibility do you have? How easy would it be for a threat to access the OT network from the substation?
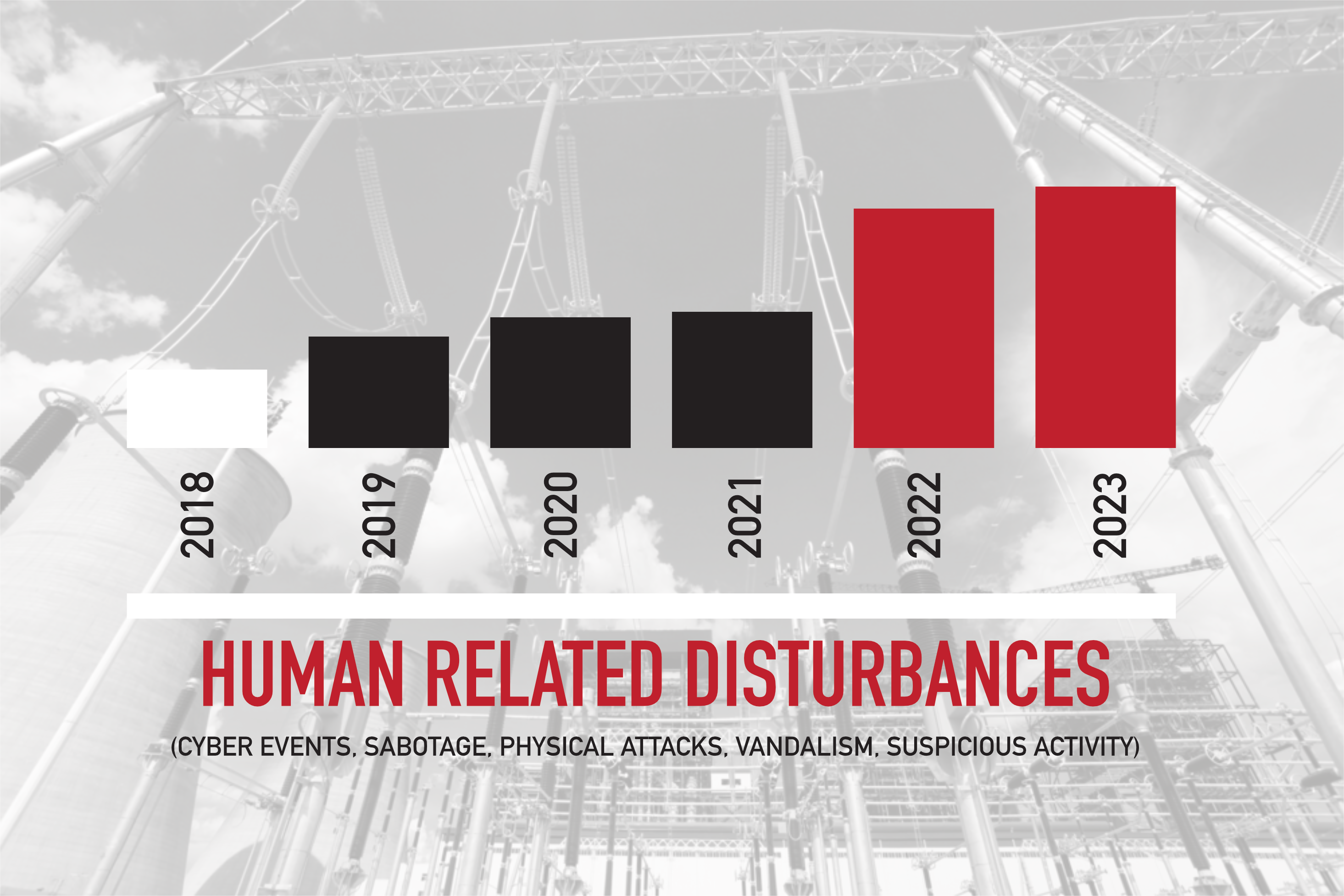
The Contextual Security Solutions Substation Audit can help organizations better understand their risk related to a substation attack. This audit includes a review of the physical controls (e.g. cameras, gates, locks, door, personnel), network security (vulnerabilities, segmentation controls), and communications security. The results from the Substation Audit are documented in a formal report and covered in an out brief. To learn more about our Substation Auditing service, or any of our other Operational Technology Reviews (Power, Water, Gas, Misc.), please click the “Schedule a Discovery Call” below.



















