Another One bites the Dust | Risk-Based Protections in a Vulnerability World
Too much work. Too few people. This is a constant battle in the cyber defense space. With the growth of attacks on software and systems, company vulnerability management platforms are maintaining a steady flow of new vulnerabilities discovered in vulnerability scanning databases. The numbers are in, and they don’t look good. Cvedetails.com, pulling from the NVD API estimates that there have been over 200,000 vulnerabilities discovered in the last 10 years alone with an average over 3000 CVEs being created each month . Blue team administrators have a good amount of their work cut out for them.
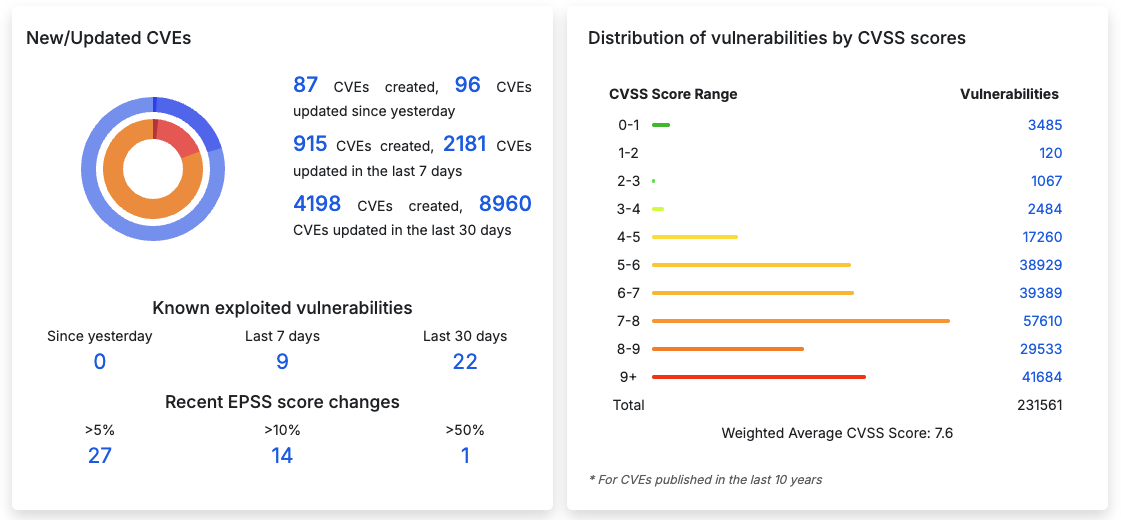
I speak directly with organizations across the nation on an annual basis and one of the biggest sticking points for them is how to deal with the constant vulnerability influx, keep up with compliance framework requirements, and not blow their entire budget on people and tools just for this one task.
Since no one has offered an answer before, I do not kid myself to believe that I’ve got the silver bullet. However, I want to speak more about this at a principled level because with most organizations that I have looked at, the soundest principles have always made the soundest security. We can’t stop at vulnerability management. The scope needs to be much wider.
Security Through History
Consider the evolution of the elements that make up a castle. Common elements might include walls, turrets, a moat, drawbridge, canon batteries and more. But they didn’t all come standard with that right out of the gate. As attackers learned better strategies, defenders had to adapt. Many European castles have had many owners based on conquests and defeats from those very vulnerabilities. So how did some last for many years? They incorporated innovative defense strategies into the fabric of future designs because they learned from previous events. They thought about their kingdom, location, people, and defenses and built castles that still endure today.
When the prize is good enough and the attacker is persistent enough, the red team (almost) always wins. Where have they failed? Prepared, equipped, aware defenders. If a king knows the attacking army is coming, is aware of his weak points, and is able to muster a defense equal or greater than the attack, he will succeed 9/10 times.
This is why vulnerability management is just one element of defense that often gets outsized importance. Yes, we can see critical CVSS scores in our latest report. Yes, some of them can be very bad if left un remediated. But we can’t just remediate all the critical and high severity vulnerabilities (assuming we can do even that) and believe we’re in good shape. While those have a higher CVSS score, they have been shown to not always be the clearest path to compromise. Our own data show that informational, low, and medium severity data can sometimes be the surprising killer that organizations were not prepared to see on their report. We need to look organizationally at who we are, how we function, and assess what our actual risks are. If I know my organization’s biggest weaknesses, struggles, and prizes, I know how to architect defenses proactively. But vulnerability management is inherently a reactive system and waiting behind a reactive system is a one-way ticket to seeing your worst nightmare get a CVSS score, and you can’t do anything about it but call your cyber insurance.
How do we get prepared, equipped, and aware? We’ve got to look at the whole of the organization. Who are we, what do we have of value, and what are our wholistic protections around it. How do all of our corporate pieces connect and work to make us both run efficiently, and ward off the bad guys? We offer multiple ways to assess risk in your organization and can prepare you to meet challenges head on, not react to them. In each job that I do, I seek to provide clients with strategies to look ahead and where they are weak and plan for those in advance. Assessing risk is a timeless exercise that is still effective in understanding who you are and how to protect your assets. In the next blog, I will explain how to get out from behind “resolve all the things” and help put you in the driver’s seat of your program.






















